ASV SCANNING
Approved Scanning Vendor
Regular vulnerability scans from an approved scanning vendor are a core component of PCI DSS compliance. After thousands of scans completed, we can help you uncover all vulnerabilities in your environment and achieve your attestation certificate.
PCI SSC Approved Scanning Vendor (ASV)
In order to be PCI DSS compliant, your organization must adhere to requirement 11.2: “Run internal and external network vulnerability scans at least quarterly and after any significant change in the network. Quarterly external scans must be performed by an Approved Scanning Vendor (ASV).”
We use comprehensive network scans to identify vulnerabilities in your organization’s environment and provide remediation assistance and recommendations to help you achieve your quarterly Attestation of Scanning Compliance. With thousands of approved scans under our belts, nobody is better qualified to help your organization through all aspects of PCI DSS compliance.
OUR DIFFERENTIATORS
Enhanced Security Posture
By regularly identifying and correcting vulnerabilities, organizations can improve their overall security posture and reduce the risk of security breaches.
Compliance Management
Our ASV Scan Portal simplifies the process of meeting compliance requirements, such as PCI DSS, by automating vulnerability scanning and providing actionable insights.
Time and Cost Savings
By streamlining the vulnerability management process, our solution saves organizations valuable time and resources that can be redirected towards other critical security initiatives.
Continuous Improvement
Regular scanning and reporting enable organizations to track their progress and continuously improve their security posture.
Our portal is a cutting-edge, comprehensive solution designed to assist organizations in conducting their PCI-DSS ASV scans efficiently and effectively. By combining the power of advanced scanning technology with user-friendly interfaces, we have created a portal that simplifies the process of identifying, analyzing, and resolving security vulnerabilities for our customers. Contact us today to learn more about ASV Scanning with Novawatch.
ASV SCANNING PORTAL
NovaScan: Your PCI ASV Scanning Portal for Simplified Compliance
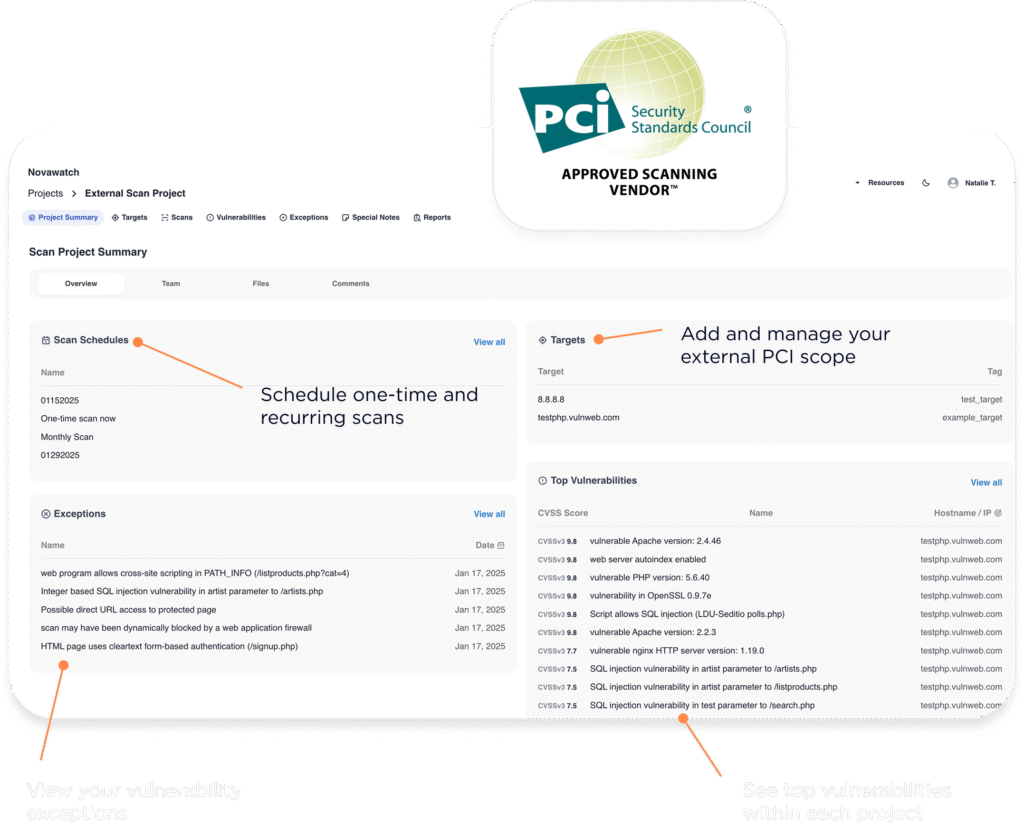
We start by configuring a custom PCI portal for your company to conduct ASV scans and generate your Self-Assessment Questionnaire (SAQ) report, if needed. Once the portal has been activated, a Novawatch security consultant will walk you through using it and provide you with recommendations for conducting and understanding the results of your first scan.
KEY BENEFITS
Minimize Risk and Ensure Compliance with Our PCI SSC Approved Scanning Service
A Novawatch security team will begin by identifying all external facing IPs that are in scope for vulnerability scanning.
Our team will coordinate with your team to schedule scanning activities. Your productivity is a priority, which is why we make sure our assessments never interfere with your organization’s workflow.
Once the external ASV scans are complete, the Novawatch team will review scan results internally to ensure accuracy. If any vulnerability exists, the consultant will offer customized remediation consulting and perform retesting (if necessary).
Once your organization has passed the ASV scan, Novawatch will issue an Attestation of Scanning for submission to acquirers, processors, gateways, and other PCI stakeholders. We also provide detailed Technical Reports, including an Executive Summary, for your information and records.

Entrust Novawatch to Be Your Approved Scanning Vendor
As a qualified ASV (approved by the PCI Security Standards Council), our goal is to assist merchants and service providers in becoming, and staying, PCI DSS compliant.








